Red Team Report Template
This is best viewed in light mode or the document template.
This is a sample red team report. Use this as a starting point or reference to create or enhance your own custom template.
Red Team Report
[ Company Name and Logo ] i♥redteams, Inc. 
[ TARGET NAME / CUSTOMER ] ABC Industries, Inc.
[ Report Title ] ABC Industries, Inc. Red Team Engagement
[ DATE ] December 2018
Executive Summary
[ Red Team ] performed a Red Team engagement on [ CLIENT NAME ] domain from [ DATES ].
The engagement performed by [ Red Team ] employed real-world adversary techniques to target the systems under test. The sequence of activities in this approach involves open source intelligence (OSINT) collection, enumeration, exploitation, and attack in order to perform goal specific operational impacts. The goals included:
- [ Goal 1 ]
- [ Goal 2 ]
- [ Goal x ]
Although Red Team engagements are focused on security weaknesses, several positive observations were made:
- [ Observation 1 ]
- [ Observation 2 ]
- [ Observation x ]
Specific observations for this assessment are outlined in the “Observations and Recommendations” section of this report. The following list is a brief summary of these observations:
- [ Observation 1 ]
- [ Observation 2 ]
- [ Observation x ]
A summary of goals and objectives achieved by [ Red Team ] include the following:
- [ Goal 1 Results ]
- [ Goal 2 Results ]
- [ Goal x Results ]
[ Red Team ] has provided specific recommendations for reducing the risks imposed by these issues in the “Observations and Recommendations” section of this report. [ Red Team ] appreciates the opportunity to support [ CLIENT NAME ] with its computer security. We look forward to assisting you and the [ CLIENT NAME ] IT Staff in future endeavors.
Table of Contents
[ TOC GOES HERE ]
Methodology and Goals
Red Team engagements performed by [ Red Team ] employ real-world adversary techniques to target the systems under test. [ Red Team ] uses a red team model emulating real adversary tools, techniques and procedures (TTPs) driven by attack scenarios and goals. Unlike a traditional penetration test, the red team model allows for the testing of the entire security scope of an organization to include people, processes and technology. The three major Red Team phases were used during the engagement to accurately emulate a realistic threat. Get In, Stay In, and Act. The sequence of activities in this approach involves open source intelligence (OSINT) collection, enumeration, exploitation, and attack. Information gathered during OSINT collection is used in conjunction with passive and active enumeration. Enumeration information typically yields details about specific hardware, services, and software running on remote machines. The next phase involves analyzing all accumulated information to identify potential attack vectors. If a weakness can be exploited, operators attempt to obtain additional access into the network or system and to collect sensitive system information to create effects and demonstrate impact to the customer. Vetted tools, methodologies, and operator experience were employed to prevent unintentional disruption, degradation or denial of service to the customer.
The goals included:
- [ Goal 1 ]
- [ Goal 2 ]
- [ Goal x ]
Scenario and Scope
Scenario
The Red Team engagement was based on the Assumed Breach Model utilizing external command and control. A coordinated phishing attack was used to begin the test and involved the support of a trusted agent. The coordinated phish was followed by a phishing attack against real-world users who did not have any knowledge of the engagement. The approach of the Assumed Breach Model allows the test to begin quickly and later use access gained from the phishing attack to validate actions.
Scope
The scope identified by [ CLIENT NAME ] is to include the subnet: 111.222.333.444/24. Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text
Micellaneous
Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text Normal text
- List Bullet
- List Bullet
- List Bullet
Attack Narrative
The following section outlines the sequence of events and highlights the key points during the engagement.
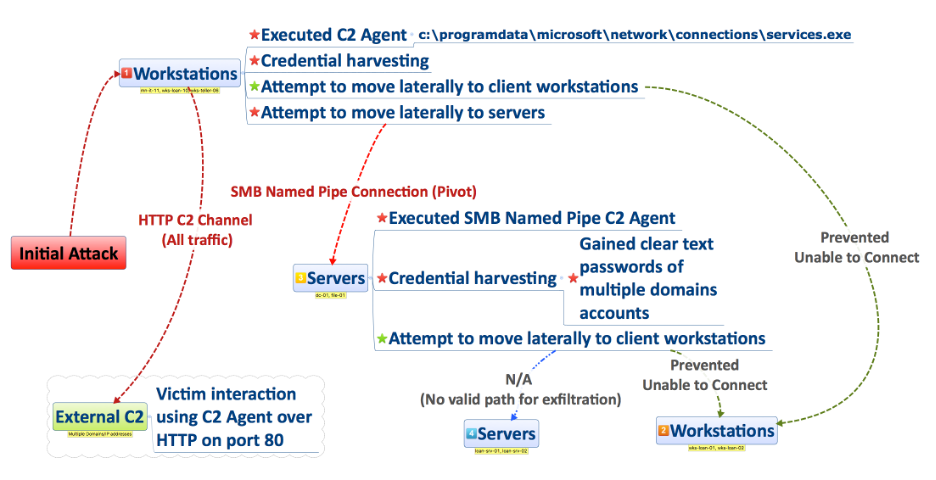
Critical Step 1
[ Crital step details. Include enough details to describe the observations ]
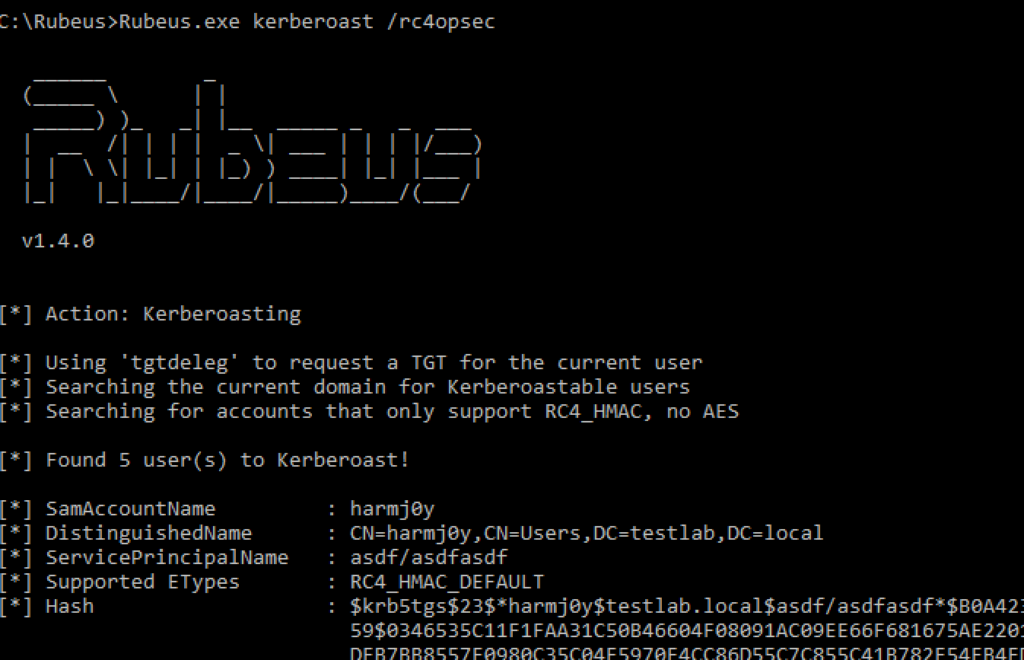
Critical Step 2
[ Crital step details. Include enough details to describe the observations ]

Observations an Recommendations
The following section is intended to discuss specific scenarios that contributed to the compromise. The observations might be individually exploitable, an element of the overall compromise, or serve as a condition that directly impacts the ability to move laterally, escalate privileges, or persist.
Observation 1
[ Observation details ]
Recommendation (Optional)
[ Recommendation details ]
Validation (Optional)
[ Validation details ]
Observation 2
[ Observation details ]
Recommendation (Optional)
[ Recommendation details ]
Validation (Optional)
[ Validation details ]
Conclusion
[ Red Team ] performed a Red Team engagement at the request of [ CLIENT NAME ] to determine the full impact of a realistic threat. The [ Red Team ] team identified several exploitable vulnerabilities that were leveraged to establish a foothold, escalate privileges, expand access across the domain, and move proprietary information out of the network. [ Red Team ] assesses that an external threat can successfully compromise [ CLIENT NAME ] systems based on the path demonstrated during the assessment. No highly specialized exploits or tools were used or required to perform any of the actions described within this report. [ Red Team ] used a publicly available attack framework for nearly all exploitation activities. The technical skill level required to conduct individual actions ranges from low to intermediate. The required technical capability and level of access that was achieved by chaining these vulnerabilities is a cause for concern. Critical exposures and observations include [ observation ], [ observation ], and [ observation ]. [ Red Team ] operators demonstrated that an adversary with an organized phishing campaign could potentially compromise the [ CLIENT NAME ] domain and remotely collect sensitive data or observe, disrupt or deny business operations. Overall, the Red Team was able to accomplish threat objectives and it is our hope that the security posture of [ CLIENT NAME ] systems will be improved as a result of the efforts.