What is Red Teaming?
Red teaming is a goal oriented process driven by threat tactics. The focus is on training or measuring a blue team's ability to defend against this threat. Defense covers protection, detection, response, and recovery. PDRR
What is Red Teaming?
Definition: Red Teaming is the process of using Tactics, Techniques, and Procedures (TTPs) to emulate a real-world threat with the goals of training and measuring the effectiveness of the people, processes, and technology used to defend an environment.
Red teaming is NOT a hunt for vulnerabilities, flaws, bugs, etc. The goal is to understand security operations as a whole (people, processes, and technology). The result of a red team engagement may identify vulnerabilities, but more importantly, red teaming provides an understanding of blue's capability to impact a threat's ability to operate.
Why Red Team?
- Measure the effectiveness of the people, processes, and technology used to defend a network. How do you know if blue TTPs are effective?
- Train and/or measure Blue Teams ability to impact a threat Blue teams need practice. Better to practice on a helpful threat that a real one
- Test and understand specific threats or threat scenarios Red team engagements can be designed to exercise custom scenarios. Scenarios can include zero-days, ransom-ware attacks, or other unique attacks.
Threat Gets a Vote
Dig deeper in the need for the threat perspective here. Threat Gets a Vote - Applying a Threat-Based Approach to Security Testing
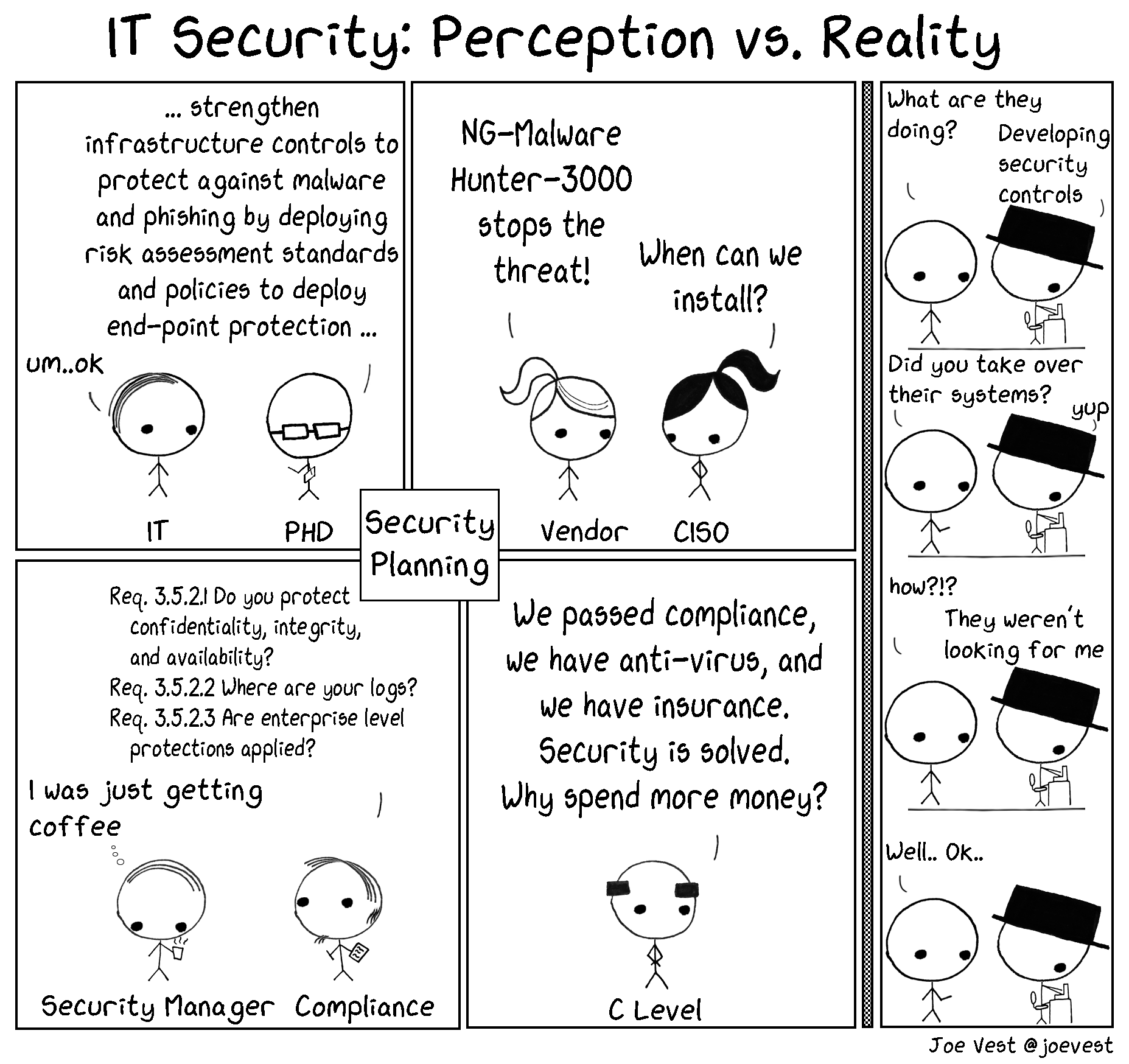
How often do security defenders ask the bad-guy how or what they will do? Many organization develop security defenses without fully understanding what is important to a threat. Red teaming provides defenders an understanding of how a threat operates in a safe controlled process.
Better to learn and practice with a Red Team than a real buy guy... anonymous blue teamer
Red Teaming vs Penetration Testing vs Vulnerability Testing
Follow this link for a comparison of security testing types.
Red Team Engagement vs Penetration Test vs Vulnerability Assessment